[BUUCTF]jarvisoj_level0 1
题目:https://buuoj.cn/challenges#jarvisoj_level0
失忆了…
main:
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
vulnerable_function()
1 | ssize_t vulnerable_function() |
而且很轻易能看到有system函数和/bin/sh,要素很齐全。记一下这个地址0x400596
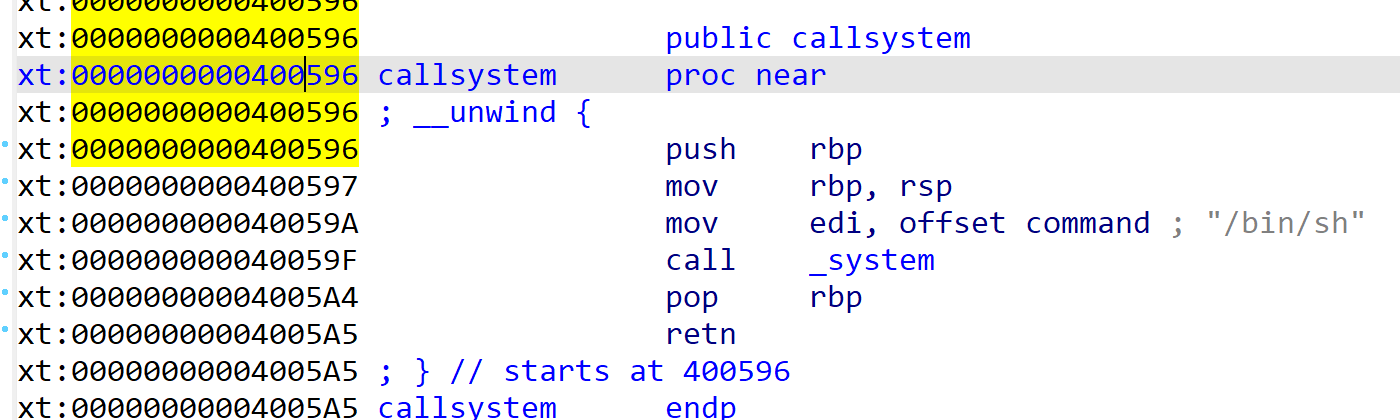
忘了checksec了()总之就是栈溢出,大概是ret2text
1 | from pwn import * |